CVE-2020-15247 (GCVE-0-2020-15247)
Vulnerability from cvelistv5
Published
2020-11-23 19:35
Modified
2024-08-04 13:08
Severity ?
VLAI Severity ?
EPSS score ?
CWE
- CWE-862 - Missing Authorization
Summary
October is a free, open-source, self-hosted CMS platform based on the Laravel PHP Framework. In October CMS from version 1.0.319 and before version 1.0.469, an authenticated backend user with the cms.manage_pages, cms.manage_layouts, or cms.manage_partials permissions who would normally not be permitted to provide PHP code to be executed by the CMS due to cms.enableSafeMode being enabled is able to write specific Twig code to escape the Twig sandbox and execute arbitrary PHP. This is not a problem for anyone that trusts their users with those permissions to normally write & manage PHP within the CMS by not having cms.enableSafeMode enabled, but would be a problem for anyone relying on cms.enableSafeMode to ensure that users with those permissions in production do not have access to write & execute arbitrary PHP. Issue has been patched in Build 469 (v1.0.469) and v1.1.0.
References
| ► | URL | Tags | |
|---|---|---|---|
|
|
|||
Impacted products
| Vendor | Product | Version | ||
|---|---|---|---|---|
| octobercms | october |
Version: >= 1.0.319, < 1.0.469 |
{
"containers": {
"adp": [
{
"providerMetadata": {
"dateUpdated": "2024-08-04T13:08:23.232Z",
"orgId": "af854a3a-2127-422b-91ae-364da2661108",
"shortName": "CVE"
},
"references": [
{
"tags": [
"x_refsource_CONFIRM",
"x_transferred"
],
"url": "https://github.com/octobercms/october/security/advisories/GHSA-94vp-rmqv-5875"
},
{
"tags": [
"x_refsource_MISC",
"x_transferred"
],
"url": "https://github.com/octobercms/october/commit/4c650bb775ab849e48202a4923bac93bd74f9982"
}
],
"title": "CVE Program Container"
}
],
"cna": {
"affected": [
{
"product": "october",
"vendor": "octobercms",
"versions": [
{
"status": "affected",
"version": "\u003e= 1.0.319, \u003c 1.0.469"
}
]
}
],
"descriptions": [
{
"lang": "en",
"value": "October is a free, open-source, self-hosted CMS platform based on the Laravel PHP Framework. In October CMS from version 1.0.319 and before version 1.0.469, an authenticated backend user with the cms.manage_pages, cms.manage_layouts, or cms.manage_partials permissions who would normally not be permitted to provide PHP code to be executed by the CMS due to cms.enableSafeMode being enabled is able to write specific Twig code to escape the Twig sandbox and execute arbitrary PHP. This is not a problem for anyone that trusts their users with those permissions to normally write \u0026 manage PHP within the CMS by not having cms.enableSafeMode enabled, but would be a problem for anyone relying on cms.enableSafeMode to ensure that users with those permissions in production do not have access to write \u0026 execute arbitrary PHP. Issue has been patched in Build 469 (v1.0.469) and v1.1.0."
}
],
"metrics": [
{
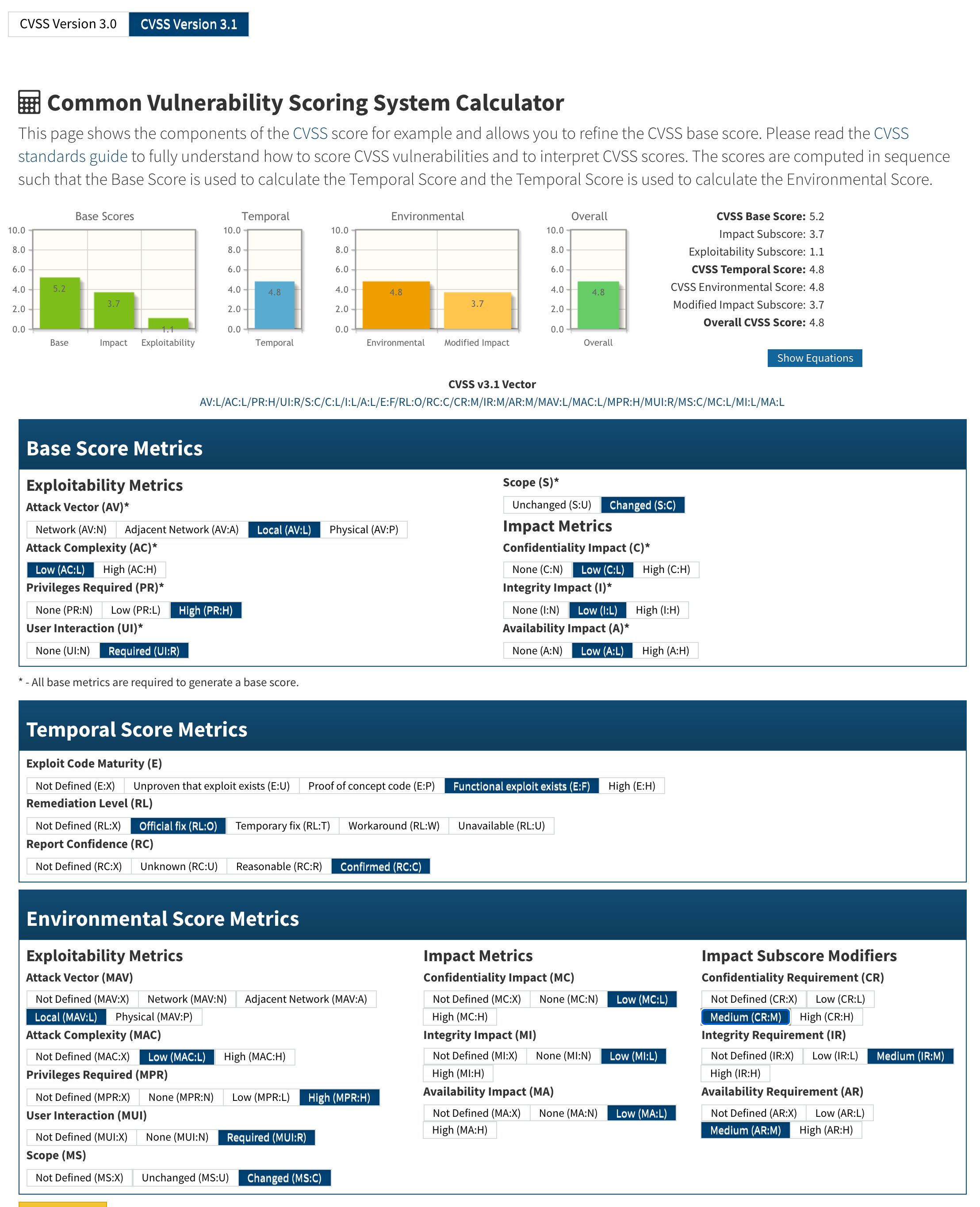
"cvssV3_1": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "LOW",
"baseScore": 5.2,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:L",
"version": "3.1"
}
}
],
"problemTypes": [
{
"descriptions": [
{
"cweId": "CWE-862",
"description": "CWE-862 Missing Authorization",
"lang": "en",
"type": "CWE"
}
]
}
],
"providerMetadata": {
"dateUpdated": "2020-11-23T19:35:13",
"orgId": "a0819718-46f1-4df5-94e2-005712e83aaa",
"shortName": "GitHub_M"
},
"references": [
{
"tags": [
"x_refsource_CONFIRM"
],
"url": "https://github.com/octobercms/october/security/advisories/GHSA-94vp-rmqv-5875"
},
{
"tags": [
"x_refsource_MISC"
],
"url": "https://github.com/octobercms/october/commit/4c650bb775ab849e48202a4923bac93bd74f9982"
}
],
"source": {
"advisory": "GHSA-94vp-rmqv-5875",
"discovery": "UNKNOWN"
},
"title": "Twig Sandbox Escape by authenticated users with access to editing CMS templates when safemode is enabled.",
"x_legacyV4Record": {
"CVE_data_meta": {
"ASSIGNER": "security-advisories@github.com",
"ID": "CVE-2020-15247",
"STATE": "PUBLIC",
"TITLE": "Twig Sandbox Escape by authenticated users with access to editing CMS templates when safemode is enabled."
},
"affects": {
"vendor": {
"vendor_data": [
{
"product": {
"product_data": [
{
"product_name": "october",
"version": {
"version_data": [
{
"version_value": "\u003e= 1.0.319, \u003c 1.0.469"
}
]
}
}
]
},
"vendor_name": "octobercms"
}
]
}
},
"data_format": "MITRE",
"data_type": "CVE",
"data_version": "4.0",
"description": {
"description_data": [
{
"lang": "eng",
"value": "October is a free, open-source, self-hosted CMS platform based on the Laravel PHP Framework. In October CMS from version 1.0.319 and before version 1.0.469, an authenticated backend user with the cms.manage_pages, cms.manage_layouts, or cms.manage_partials permissions who would normally not be permitted to provide PHP code to be executed by the CMS due to cms.enableSafeMode being enabled is able to write specific Twig code to escape the Twig sandbox and execute arbitrary PHP. This is not a problem for anyone that trusts their users with those permissions to normally write \u0026 manage PHP within the CMS by not having cms.enableSafeMode enabled, but would be a problem for anyone relying on cms.enableSafeMode to ensure that users with those permissions in production do not have access to write \u0026 execute arbitrary PHP. Issue has been patched in Build 469 (v1.0.469) and v1.1.0."
}
]
},
"impact": {
"cvss": {
"attackComplexity": "LOW",
"attackVector": "LOCAL",
"availabilityImpact": "LOW",
"baseScore": 5.2,
"baseSeverity": "MEDIUM",
"confidentialityImpact": "LOW",
"integrityImpact": "LOW",
"privilegesRequired": "HIGH",
"scope": "CHANGED",
"userInteraction": "REQUIRED",
"vectorString": "CVSS:3.1/AV:L/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:L",
"version": "3.1"
}
},
"problemtype": {
"problemtype_data": [
{
"description": [
{
"lang": "eng",
"value": "CWE-862 Missing Authorization"
}
]
}
]
},
"references": {
"reference_data": [
{
"name": "https://github.com/octobercms/october/security/advisories/GHSA-94vp-rmqv-5875",
"refsource": "CONFIRM",
"url": "https://github.com/octobercms/october/security/advisories/GHSA-94vp-rmqv-5875"
},
{
"name": "https://github.com/octobercms/october/commit/4c650bb775ab849e48202a4923bac93bd74f9982",
"refsource": "MISC",
"url": "https://github.com/octobercms/october/commit/4c650bb775ab849e48202a4923bac93bd74f9982"
}
]
},
"source": {
"advisory": "GHSA-94vp-rmqv-5875",
"discovery": "UNKNOWN"
}
}
}
},
"cveMetadata": {
"assignerOrgId": "a0819718-46f1-4df5-94e2-005712e83aaa",
"assignerShortName": "GitHub_M",
"cveId": "CVE-2020-15247",
"datePublished": "2020-11-23T19:35:14",
"dateReserved": "2020-06-25T00:00:00",
"dateUpdated": "2024-08-04T13:08:23.232Z",
"state": "PUBLISHED"
},
"dataType": "CVE_RECORD",
"dataVersion": "5.1",
"vulnerability-lookup:meta": {
"nvd": "{\"cve\":{\"id\":\"CVE-2020-15247\",\"sourceIdentifier\":\"security-advisories@github.com\",\"published\":\"2020-11-23T20:15:12.383\",\"lastModified\":\"2024-11-21T05:05:10.993\",\"vulnStatus\":\"Modified\",\"cveTags\":[],\"descriptions\":[{\"lang\":\"en\",\"value\":\"October is a free, open-source, self-hosted CMS platform based on the Laravel PHP Framework. In October CMS from version 1.0.319 and before version 1.0.469, an authenticated backend user with the cms.manage_pages, cms.manage_layouts, or cms.manage_partials permissions who would normally not be permitted to provide PHP code to be executed by the CMS due to cms.enableSafeMode being enabled is able to write specific Twig code to escape the Twig sandbox and execute arbitrary PHP. This is not a problem for anyone that trusts their users with those permissions to normally write \u0026 manage PHP within the CMS by not having cms.enableSafeMode enabled, but would be a problem for anyone relying on cms.enableSafeMode to ensure that users with those permissions in production do not have access to write \u0026 execute arbitrary PHP. Issue has been patched in Build 469 (v1.0.469) and v1.1.0.\"},{\"lang\":\"es\",\"value\":\"October es una plataforma CMS gratuita, de c\u00f3digo abierto y autohosteada basada en Laravel PHP Framework.\u0026#xa0;En October CMS desde la versi\u00f3n 1.0.319 y anterior a versi\u00f3n 1.0.469, un usuario del backend autenticado con los permisos cms.manage_pages, cms.manage_layouts o cms.manage_partials que normalmente no estar\u00eda autorizado a proporcionar c\u00f3digo PHP para ser ejecutado por el CMS debido a que cms.enableSafeMode est\u00e1 habilitado, es capaz de escribir c\u00f3digo espec\u00edfico de Twig para escapar del sandbox de Twig y ejecutar PHP arbitrario.\u0026#xa0;Esto no es un problema para cualquiera que conf\u00ede en sus usuarios con esos permisos para escribir y administrar PHP normalmente dentro del CMS al no tener cms.enableSafeMode habilitado, pero ser\u00eda un problema para cualquiera que conf\u00ede en cms.enableSafeMode para asegurarse de que los usuarios con esos permisos en producci\u00f3n no poseen acceso para escribir y ejecutar PHP arbitrario\"}],\"metrics\":{\"cvssMetricV31\":[{\"source\":\"security-advisories@github.com\",\"type\":\"Secondary\",\"cvssData\":{\"version\":\"3.1\",\"vectorString\":\"CVSS:3.1/AV:L/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:L\",\"baseScore\":5.2,\"baseSeverity\":\"MEDIUM\",\"attackVector\":\"LOCAL\",\"attackComplexity\":\"LOW\",\"privilegesRequired\":\"HIGH\",\"userInteraction\":\"REQUIRED\",\"scope\":\"CHANGED\",\"confidentialityImpact\":\"LOW\",\"integrityImpact\":\"LOW\",\"availabilityImpact\":\"LOW\"},\"exploitabilityScore\":1.1,\"impactScore\":3.7},{\"source\":\"nvd@nist.gov\",\"type\":\"Primary\",\"cvssData\":{\"version\":\"3.1\",\"vectorString\":\"CVSS:3.1/AV:L/AC:L/PR:H/UI:R/S:C/C:L/I:L/A:L\",\"baseScore\":5.2,\"baseSeverity\":\"MEDIUM\",\"attackVector\":\"LOCAL\",\"attackComplexity\":\"LOW\",\"privilegesRequired\":\"HIGH\",\"userInteraction\":\"REQUIRED\",\"scope\":\"CHANGED\",\"confidentialityImpact\":\"LOW\",\"integrityImpact\":\"LOW\",\"availabilityImpact\":\"LOW\"},\"exploitabilityScore\":1.1,\"impactScore\":3.7}],\"cvssMetricV2\":[{\"source\":\"nvd@nist.gov\",\"type\":\"Primary\",\"cvssData\":{\"version\":\"2.0\",\"vectorString\":\"AV:L/AC:M/Au:N/C:P/I:P/A:P\",\"baseScore\":4.4,\"accessVector\":\"LOCAL\",\"accessComplexity\":\"MEDIUM\",\"authentication\":\"NONE\",\"confidentialityImpact\":\"PARTIAL\",\"integrityImpact\":\"PARTIAL\",\"availabilityImpact\":\"PARTIAL\"},\"baseSeverity\":\"MEDIUM\",\"exploitabilityScore\":3.4,\"impactScore\":6.4,\"acInsufInfo\":false,\"obtainAllPrivilege\":false,\"obtainUserPrivilege\":false,\"obtainOtherPrivilege\":false,\"userInteractionRequired\":true}]},\"weaknesses\":[{\"source\":\"security-advisories@github.com\",\"type\":\"Secondary\",\"description\":[{\"lang\":\"en\",\"value\":\"CWE-862\"}]},{\"source\":\"nvd@nist.gov\",\"type\":\"Primary\",\"description\":[{\"lang\":\"en\",\"value\":\"NVD-CWE-Other\"}]}],\"configurations\":[{\"nodes\":[{\"operator\":\"OR\",\"negate\":false,\"cpeMatch\":[{\"vulnerable\":true,\"criteria\":\"cpe:2.3:a:octobercms:october:*:*:*:*:*:*:*:*\",\"versionStartIncluding\":\"1.0.319\",\"versionEndExcluding\":\"1.0.469\",\"matchCriteriaId\":\"ABEFA590-9054-45DD-A177-D5EBEA49C5B7\"}]}]}],\"references\":[{\"url\":\"https://github.com/octobercms/october/commit/4c650bb775ab849e48202a4923bac93bd74f9982\",\"source\":\"security-advisories@github.com\",\"tags\":[\"Patch\",\"Third Party Advisory\"]},{\"url\":\"https://github.com/octobercms/october/security/advisories/GHSA-94vp-rmqv-5875\",\"source\":\"security-advisories@github.com\",\"tags\":[\"Third Party Advisory\"]},{\"url\":\"https://github.com/octobercms/october/commit/4c650bb775ab849e48202a4923bac93bd74f9982\",\"source\":\"af854a3a-2127-422b-91ae-364da2661108\",\"tags\":[\"Patch\",\"Third Party Advisory\"]},{\"url\":\"https://github.com/octobercms/october/security/advisories/GHSA-94vp-rmqv-5875\",\"source\":\"af854a3a-2127-422b-91ae-364da2661108\",\"tags\":[\"Third Party Advisory\"]}]}}"
}
}
Loading…
Loading…
Sightings
| Author | Source | Type | Date |
|---|
Nomenclature
- Seen: The vulnerability was mentioned, discussed, or seen somewhere by the user.
- Confirmed: The vulnerability is confirmed from an analyst perspective.
- Exploited: This vulnerability was exploited and seen by the user reporting the sighting.
- Patched: This vulnerability was successfully patched by the user reporting the sighting.
- Not exploited: This vulnerability was not exploited or seen by the user reporting the sighting.
- Not confirmed: The user expresses doubt about the veracity of the vulnerability.
- Not patched: This vulnerability was not successfully patched by the user reporting the sighting.
Loading…
Loading…